Introduction to Linux
"Linux is an open source Unix-Like operating system based on the linux kernal..." yeah this blog isn't about a lecture on linux but how to use the system and utilise it for cyber security. What you need to know is that:
Linux is an operating system
It has things called "Distributions" which are: Ubuntu, Debian, Arch, Fedora, etc.
You have a lot of control over everything and linux won't warn you - wanna delete your root directory? Go for it!
This amount of customisation and control over your system makes linux an ideal system to master.
Using Linux
We will go into:
Linux File Systems
Linux Commands
Exercises
File Systems
Files in linux operate on a hierarchy type model for its files and directories:
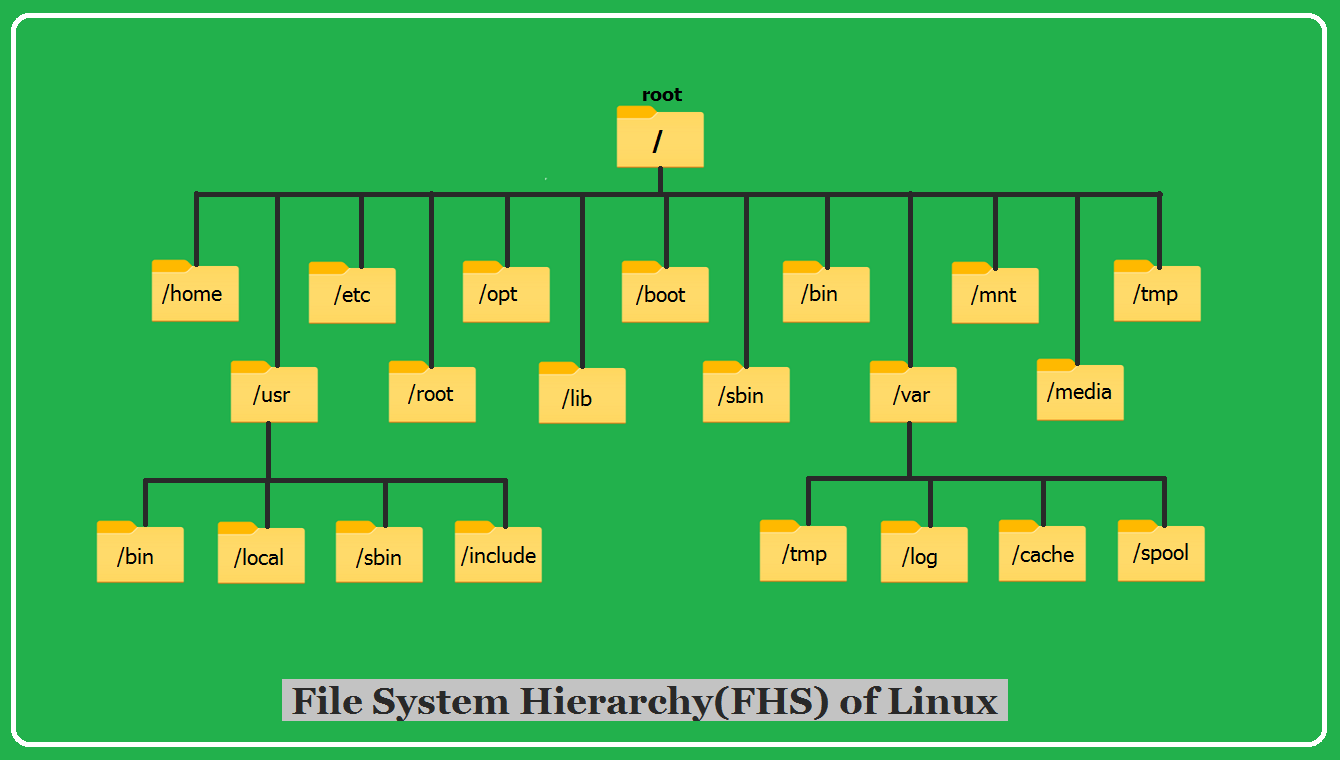
The top part of the 'tree' is called the root - it houses all of your directories, while everything else is called a 'node'. Each 'parent' node can have a 'child' node, which is to say, a folder inside of another folder.
Content Types
There are 4 major types of content stored in a file system:
Persistent: Contents that will be persistent after a system reboot. (Systems and Application configuration settings)
Runtime: Content generated by a running process (Usually deleted by a reboot)
Variable/Dynamic: The content of these can be appended or modified by processes running on the system
Static Content: Content that remains unchanged unless edited or configured
/etc
Contains configuration files used by system services
/root
This is a home directory for the Linux superuser account, root
/boot
Contains all the files needed to start the boot process.
/home
This is where standard users store their personal configurations and data such as Documents, Videos, Music etc
/var
Has variable data that is required to persist between boots – databases, log files, mails, cache directories, Web data etc
/tmp
Stores temporary files. All Linux users can write to this directory. Files older than 10 days are deleted automatically.
/usr
This directory contains shared libraries, installed software, and read-only program data. Some of the important subdirectories include: /usr/bin: Mostly user commands are located here. /usr/sbin: Hosts System administrative commands that required privilege escalation to run. /usr/local: For locally customized software.
/dev
This contains special device files used by the system to access hardware.
/run
The processes started since the last boot stores their runtime data here, e.g. process ID files and lock files. These contents are recreated on reboot.
Shortcuts
Some helpful shortcuts:
Navigating your terminal
The terminal is the most essential part of your linux system (other than the root, boot, uhh everything else) learning how to use it will make you much faster in navigating, programming, and hacking. Skipping this step will only bring you pain trust me.
Basic Commands
There are many more commands that we will come across but we will get to them later. For now, let's look at flags and wildcards.
Flags
Wildcards
Wildcards are special characters that do specific things or target specific items based on the users' input
Exercises
Solve these exercises to get you comfortable with using Linux. You can always refer to the man page or back here for references.
Last updated